Automatically run VSCode commands
A typical engineering interview in the company I work for includes a “take-home-exercise”, which as the name suggests contains a task that has to be completed within a given time-limit at home.
Upon completion those tasks will be submitted back to us and reviewed by senior engineers within the company.
Recently we had to tackle the question: “Can a malicious actor hide arbitrary code in the submitted exercise? Taking into account that 74% of professionals use VSCode .”
Yes, they can! But…
1 Requirements
A few requirements must be met:
- VSCode needs to be in use
- The submitted code is not checked for differences before opening in VSCode
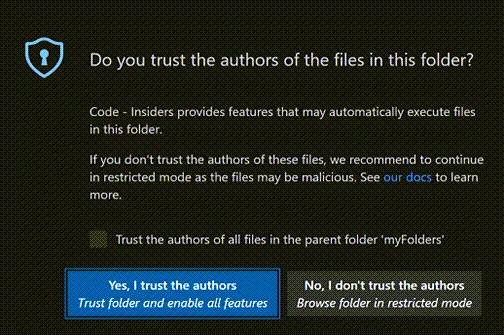
- “Trust the author” is selected on the startup screen
In this case it’s possible to execute code in the background.
2 Breakdown
VSCode allows to define a set of tasks as the part of a project.
When opening a new folder for a first time, a dialog will be displayed asking if you want to trust a workspace . Trusting a workspace will allow automatic tasks to run.
These tasks typically reside within the .vscode/tasks.json, a folder that is hidden by default as specified in the default behaviour of ls.
Making it harder to detect on task submission.
Filenames beginning with a <period> ( ’.’ ) and any associated information shall not be written out unless explicitly referenced 1
I’m not going to break down the full spec , but a .vscode/tasks.json file could look like this:
{ "version": "2.0.0", "tasks": [ { "label": "Malicious code", "type": "shell", "command": "echo \"doing something malicious\"", "presentation": { "reveal": "silent", "echo": false, "revealProblems": "never" }, "runOptions": { "runOn": "folderOpen" } } ]}This code will run echo "doing something malicious" completely hidden (reveal: silent and without and output echo: false or error logging revealProblems: "never").
Scary, right?